New threats are always on the horizon, but a good security risk management approach is all about balance. George Dionisopoulos, Head of Security at Australian data centre provider, NEXTDC, explains why.

George Dionisopoulos, Head of Security, NEXTDC
Security teams play many roles in their organisations. First and foremost, we’re the frontline sentries protecting our people, data, assets and operations from attacks and accidental breaches.
Lately I’ve also been thinking we’re a little bit like builders and carpenters, too. We build and tinker with our internal and external environment daily to ensure it’s in the best possible state to sustain the organisation for the long-term.
And that doesn’t just mean the doors, walls and other barriers to the outside world – every single item within the house must be reinforced, protected and maintained. This is never a ‘set and forget’ process, because the world around us changes on a daily basis.
It is a bit like painting Sydney Harbour Bridge. When you get to the end of the process, you go back and start again. The maintenance never ends.
It’s a tough job, simply because there are so many facets to it. For instance, the more we hear about cyber-attacks in the public domain, the greater the pressure becomes to protect the organisation at all costs.
And so it should. The immediate fallout of cyber security breaches is well-documented, and potential repercussions keep many of us awake at night.
The average cost of a data breach has reached US $4.35 million, according to research by IBM, and that’s not even considering the possibilities associated with long-term brand reputational damage and loss of stakeholder confidence.
Security risk management – why balance is the key
Lately many of our customer contacts who are involved in organisational risk management report they are being asked about cyber security planning on a near daily basis. This is a positive step forward, considering that even just a few years ago, there was little appetite for it.
However, this keen focus on cyber can actually be detrimental to the broader security risk management portfolio in the longer term.
Why? Because it’s going to affect the balance. Just like a builder or carpenter, as security professionals we need to be obsessed with balance and symmetry in our work – or risk disaster.
“Just like a builder or carpenter, as security professionals we need to be obsessed with balance and symmetry in our work – or risk disaster.”
The four pillars of security risk management
When it comes to digital infrastructure, I think of a balanced security risk management portfolio as being a bit like a beautifully crafted chair. It sits solidly on four legs of equal length and width, to balance the load above it:
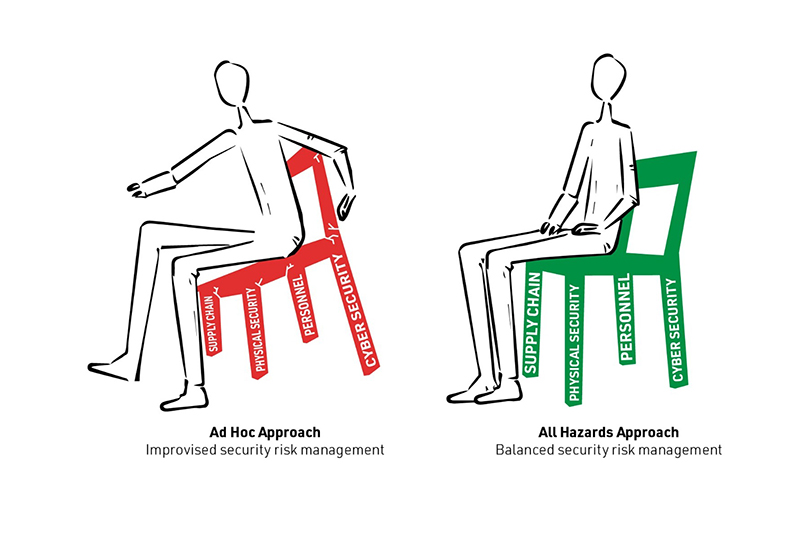
Second Leg – Physical Security: The physical environment in which your infrastructure is housed is critical. This is not only about overall surveillance and security systems – small details matter, as do the brand names on the box. How confident are you that every part of every piece of equipment in each of your facilities is guaranteed ‘secure’ to your country’s standards?
Third Leg – Personnel: Never underestimate the ‘insider risk’ – whether intentional or unintentional, your own people are likely to be responsible for the vast majority of security lapses. This risk can only be mitigated with a comprehensive programme of training and education, coupled with extensive background checks of anyone who has access to the facility.
Fourth Leg – Supply Chain: Have you factored in the potential for disruptions from your supply chain, whether through force majeure, accidents or malicious acts? Have you vetted personnel right down the supply chain, and can you ensure all equipment is installed as specified – no matter how far removed from your core operations?
The all-hazards approach
Many risks fall across more than one category, which highlights the need to take an integrated approach. For example, if you have a sub-contractor who is looking to gain access to restricted parts of your facility to wreak havoc, you have a three-pronged risk: personnel, physical and supply chain.
The risk needs to be mitigated accordingly from all three directions.
Some refer to this as an ‘all-hazards’ approach. Whatever you call it, the intent is the same: create a balanced and even distributed base, so you’ll have a more resilient overall security posture that will be able to hold up, whatever weight comes down on it.
On the other hand, if you focus on one it will come at the expense of the others and disturb the balance. Unfortunately, that is the path upon which we’re seeing some organisations embark, with their current laser-like focus on cyber security. Don’t let yours be one of them.
Let’s fix the wobbly chair together
As our physical and cyber security environments continue to merge, creating a balanced approach to security risk management of digital infrastructure requires strategic thinking and partnerships. This convergence and maintaining a balanced approach is on us, as security leaders, to identify and address.
Further reading
- Read IFSEC Insider’s interview with George Dionisopoulos, as he discusses the challenges of securing data centres, here >>
- Listen to James Willison and Sarb Sembhi discuss a converged security approach in the IFSEC Insider podcast episode below…

